Getting solid advice for small business information security can get overwhelming fast. Small business owners are often faced with long lists of tools, complex terminology, and conflicting recommendations. It can feel like enterprise-level security is the only safe option, even though the budget and resources don’t match.
The truth is simpler. Most small businesses don’t need every available security solution. What they need is a focused set of tools that address real risks without creating unnecessary complexity. When security is practical and repeatable, it becomes far more effective.
Small Businesses Are Big Targets
Cybercriminals often target small businesses because they specifically assume security is limited. Large organizations can invest heavily in dedicated security teams and advanced infrastructure, while smaller companies typically operate with lean teams and shared responsibilities.
Small teams may reuse passwords, share credentials, or rely on unmanaged devices. This vulnerability can mean increased exposure to phishing, malware attacks, credential theft, unauthorized access, and data leaks. Even one compromised account can lead to operational disruption, financial loss, and long-term reputational damage.
The good news is that many common attacks are preventable. Basic security tools, when used consistently, block a large portion of real-world threats and significantly reduce risk.
Secure Passwords and Practical Access Control
Passwords remain one of the most common weak points in business security. Reused or simple passwords make it easy for attackers to move from one compromised account to another. Once credentials are exposed, access can spread quickly across systems.
Password managers help eliminate this problem by generating strong, unique passwords and storing them securely. Employees don’t need to remember multiple logins, which reduces the temptation to reuse credentials or store them unsafely.
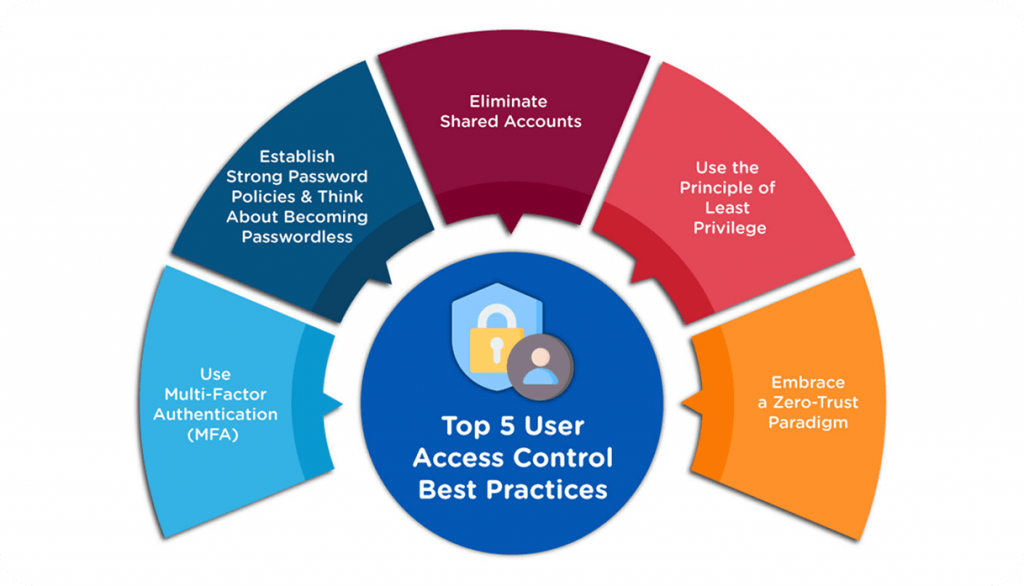
Access control is just as important as password strength. Not every employee needs access to every system at all times. Regularly reviewing permissions helps reduce unnecessary exposure. When roles change or someone leaves the company, promptly removing access limits the risk of forgotten or abused credentials.
MFA as a Baseline Requirement
Passwords alone are no longer enough to protect sensitive systems. Multi-factor authentication adds an extra layer of defense by requiring an additional verification step beyond a username and password.
While it may not seem overly protective, enabling two-factor authentication is a powerful way to prevent unauthorized access. Even if credentials are stolen, attackers still need a second factor, such as a one-time code or device confirmation, to proceed.
Most modern tools support MFA through authenticator apps, SMS codes, email verification, or hardware keys. Setup is usually quick, and the security benefit is immediate. MFA also provides early warning signals—unexpected login prompts can alert teams to attempted breaches before damage occurs.
Business VPN Use
VPNs are often misunderstood or treated as one-size-fits-all solutions. In reality, their value depends on how a business operates and where employees access systems.
Some types of VPN focus on giving employees secure remote access when they work from home or travel. These VPNs encrypt data in transit, helping protect sensitive information when employees use public or unsecured networks.
Other VPN configurations connect offices or internal systems across locations. For many small businesses, a simple remote-access VPN is enough. Choosing the right option avoids unnecessary costs and keeps security manageable rather than overengineered.
Endpoint Protection Across All Devices
Every device connected to a business environment represents a potential entry point for attackers. Laptops, desktops, mobile phones, and tablets all need protection, especially in teams that rely on remote or hybrid work.
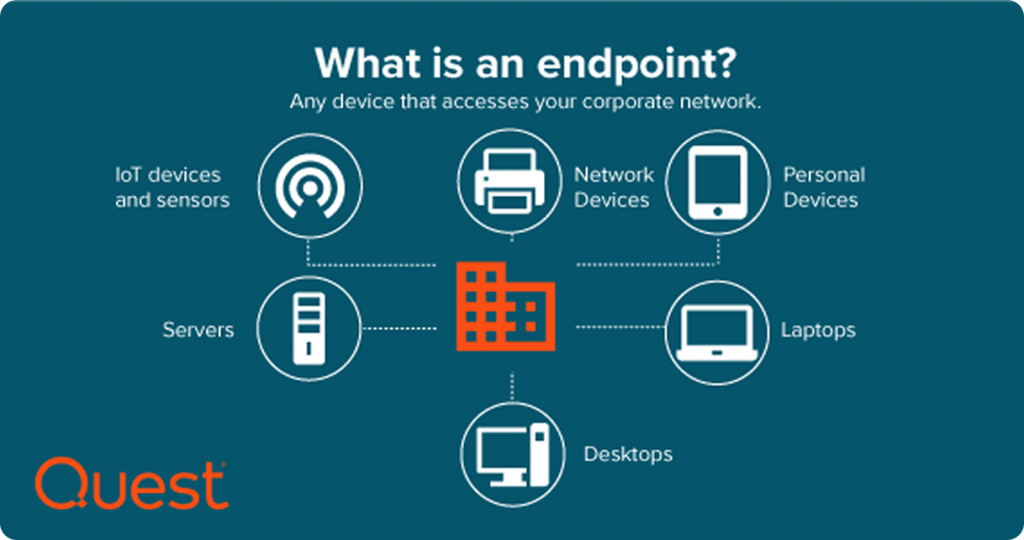
Endpoint protection tools help detect and block malware, unsafe downloads, and suspicious behavior before it causes damage. Even basic protection can prevent common threats from spreading across shared systems.
The most important factor is coverage. Protecting all devices consistently is far more effective than deploying advanced tools on only part of the device fleet. Centralized visibility also makes it easier to respond quickly if something goes wrong.
Backup and Recovery Planning
No security strategy is complete without a plan for failure. Even well-protected systems can be affected by ransomware, accidental deletion, hardware failure, or human error.
Automated backups reduce reliance on manual processes and ensure important data is copied regularly. Best practices include maintaining multiple backups, with at least one stored locally and one in the cloud. This protects against both cyber incidents and physical damage.
Just as important as backups is the ability to restore data. Periodically testing recovery processes helps ensure backups actually work when needed. Practicing recovery scenarios reduces downtime and stress during real incidents.
Monitoring, Updates, and Everyday Habits
Security tools are most effective when they fit into daily operations. Regular software updates should be applied promptly, as they often fix known vulnerabilities that attackers actively exploit.
Basic monitoring, such as alerts for unusual logins or unexpected system changes, provides early warnings before issues escalate. These signals don’t require constant attention but can make a major difference when something goes wrong.
Employee awareness also matters. Simple guidance on recognizing phishing attempts, handling sensitive information, and reporting suspicious behavior reinforces the effectiveness of technical controls. Security works best when responsibility is shared across the team.
Final Thoughts
Small businesses don’t need massive budgets or complex security stacks to stay protected. What they need is a clear focus on fundamentals: strong password practices, multi-factor authentication, reliable backups, endpoint protection, and a VPN that fits how the team works.
When these tools are supported by consistent habits and regular reviews, they provide strong protection against everyday risks. With thoughtful planning and steady execution, small businesses can protect their data, maintain customer trust, and grow without unnecessary security complexity.


